With cyber threats to the electric utility landscape increasing, what is the role of the utility C-suite in ensuring preparedness and what steps can be taken to enhance effectiveness? The reality is, effective coordination is often hampered in many utility C-suites by the inherent tensions that exist between those who take an alarmist position regarding cyber security and those who are more complacent. This discord is creating a need for a more holistic-focused approach to better understand and manage risks.
Cyber security is often times handled by small, disparate security groups that only work on a targeted subset of critical assets, leaving a larger set of unregulated components and assets across an organization exposed. In addition, C-Suite executives are often unaware of the role state-elected officials play in their own future cyber protection plans and the need for state regulators to gain assurances that public utility companies are taking necessary steps concerning cyber security.
Therefore, it is critical for C-suites to recognize the need for a holistic enterprise oversight program due to the changing nature of the cyber security landscape under their domain. They must ensure appropriate defenses are in place, as well as an effective governance framework and performance metrics are being utilized appropriately.
Key Steps in a Holistic Approach
Many organizations spend too much time focused on compliance, only implementing a handful of requirements, which can sometimes leave gaping holes in their perimeter. C-suite leaders will benefit from going beyond run of the mill health checks and gap assessments, and looking beyond just IT and operations to enhance their organization’s security posture.
The first key element to a holistic approach that leaders should be establishing is a baseline cyber security framework. Once the framework is in place, it must be accepted by the organization. Next, a more in-depth evaluation is needed to assess business systems, customer data, IT systems, operational technology (OT) systems including SCADA, physical security and all places where privacy-related information is stored.
Don’t make the mistake of letting these risk assessments sit on a shelf and collect dust once conducted. This happens when assessments are not able to be implemented because they are performed by the wrong people, so it is vital to ensure that those doing the assessments have functional experience. The most important thing for leadership to remember is to make sure the implementation strategy fits their organization, otherwise nothing will change.
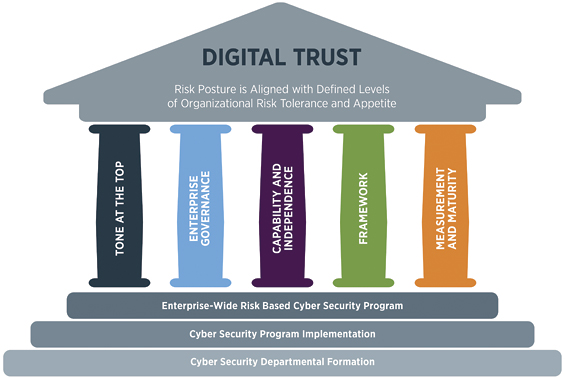
The Five Pillars
In order to properly build a risk-based cyber security program, utility leaders should use these five pillars to measure and evaluate the strength and maturity of their organization’s cyber security:
Tone At The Top –
Conversations and Communications
This first pillar focuses on the need for the C-suite to assess the organization’s readiness for change, the appetite for risk and the approach to Organizational Change Management (OCM). All of these factors should be considered carefully, with management being prepared to take on responsibility for proper cyber security and the establishment or enhancement of a cyber security framework.
At the heart of this work is the need for an executive team to be committed to the change, and communication of that commitment across all business units and employees in the organization. If leadership commitment is misunderstood by the organization, it could hinder success. The organization must assess how much and where they are willing to absorb risk, and the resource pool (people and funding) that can be committed to mitigate it. The C-suite must take active interest in the messaging to ensure consistency and commitment. This is the foundation of OCM and necessary to implement new standards of operation.
Enterprise Governance –
Organization And Defined Outcomes
The executive team needs to provide effective governance to the cyber security effort in order to maintain organizational commitment and alignment within the overall strategy. Proper accountability and monitoring should be in place to check if defined goals and outcomes are achieved. The authority to perform identified functions has to be clearly in place, documented and communicated.
Education of the executive team, board and other senior and mid-level management should also be in place to ensure proper engagement and accountability to perform and guide their organizational efforts to complete cyber security tasks. Additionally, roles must be clearly defined and operating protocols in place to provide clarity to the cyber security framework. Finally, results-focused cyber security reporting should be put in place in which the frequency and structure of the reports are reviewed and agreed upon by all parties – and these reporting standards should be updated as the framework matures.
Capability And Independence –
Authority, Personnel and Tools
Another key role for the executive team is the selection and training of cyber security personnel. They need to have the right tools, executive support and have organizational independence in terms of reporting structure – similar to auditing teams. They should have ownership and leadership of the cyber security function with C-suite backing that allows them to have enterprise authority to issue standards, incident handling leadership, and access to manage and mitigate risks with the premise that this is an expected and non-optional part of doing business. The executive team should also create and formally approve a charter for the authority of the cyber security function.
Policy Process And Procedure Framework –
Structural Framework and Program Operations
An essential part of cyber security is having multi-year implementation plans in place. The executive team should oversee and formally approve policy. Also, continued review and program updates should be scheduled to ensure that proper implementation of policy remains timely and effective. Executives need to make sure that the framework standards and policies are clear and complied with enterprise-wide.
External operational assessments of risk coverage, risk remediation and cyber security operations will help to ensure that practices are effective and in-line with organizational expectations. Security control implementation and selection, reference architecture and system security plans should all be reviewed on a regular basis to ensure relevancy and effective use.
Measurement And Maturity –
Program Monitoring, Assessment and Reporting
The executive team should assess whether it has the information and data to confirm the focus of the organization’s cyber security program is in line with expectations and ensure the appropriate level of due diligence to gather the data is evident. It is important for the C-suite and cyber security leadership to agree on metrics, frequency of operations results and program reporting reviews.
Constant vigilance and continuous improvement is needed for a program to be successful. If the proper metrics and review mechanisms are in place, the organization will have an objective assessment and real understanding of the state of their cyber security program and clarity of where improvements are truly needed.
Ultimately, the five pillar approach prioritizes risk that support the protection of the entire enterprise, not just to achieve compliance with a specific mandate such as NERC CIP. This approach consolidates cyber security efforts across the organization with a lower total cost, helping to eliminate costly redundancies that occurs when multiple parts of the utility build ad hoc cyber security mechanisms.
Having the C-suite back the implementation of an organizational cyber security framework, like the five pillars, increases the likelihood of success in implementing a holistic security program. When the entire organization, from executive ranks to the front line, are fully engaged with a security first mindset, a utility is well on its way.
About the Authors
 Justin Lowe is a cyber security expert at PA Consulting Group. Justin has more than 15 years of experience in cyber security and OT security, and the challenges of addressing security issues across the energy sector. Justin also led the development of Security Best Practices for SCADA and control systems for the UK Government’s Centre for Protection of National Infrastructure. And most recently, Justin led the development and implementation of a cyber security program for a newbuild nuclear power plant and the implementation of a cyber security program for a major utility.
Justin Lowe is a cyber security expert at PA Consulting Group. Justin has more than 15 years of experience in cyber security and OT security, and the challenges of addressing security issues across the energy sector. Justin also led the development of Security Best Practices for SCADA and control systems for the UK Government’s Centre for Protection of National Infrastructure. And most recently, Justin led the development and implementation of a cyber security program for a newbuild nuclear power plant and the implementation of a cyber security program for a major utility.
 Sean Duffy is a cyber security expert at PA Consulting Group. Sean’s experience includes: managing risk and security components of large engagements including governance (NERC & NIST), strategic visioning, and solution design and implementation; supporting clients in managing change in their organizations by developing goals, strategies, and an implementation plan to address changes needed to leverage new solution; managing legal and compliance requirements for complex information and operational technology engagements; and, leading cyber incident response planning, education & training and recovery efforts for clients.
Sean Duffy is a cyber security expert at PA Consulting Group. Sean’s experience includes: managing risk and security components of large engagements including governance (NERC & NIST), strategic visioning, and solution design and implementation; supporting clients in managing change in their organizations by developing goals, strategies, and an implementation plan to address changes needed to leverage new solution; managing legal and compliance requirements for complex information and operational technology engagements; and, leading cyber incident response planning, education & training and recovery efforts for clients.
Their findings are based on a new report from PA Consulting Group titled, “Is Your C-Suite Prepared For the Cyber Future?”








