At the edge of the distribution grid lies an inestimable number of devices (such as Solar PV and other renewable generation sources, electric vehicles, water heaters, and HVAC systems) that, if properly harnessed, could provide significant value to Smart Grid applications. While the value gained from communicating with these devices is enormous, a major roadblock to harnessing their power has been the lack of efficient, affordable, and secure communication paths.
To achieve the full promise of an interconnected power distribution system, utilities must be able to securely connect with and control end-use devices and other distribution grid assets. Doing so will give them the ability to optimize power supply portfolios, achieve grid visibility from end-use consumers to distribution substations, and use Demand Response (DR) and Distributed Energy Resources (DERs) to strategically manage system load and distribution grid operating conditions.
Implementing the kind of high-level security system needed to protect utilities and their customers from the increasing threat of cyber-attacks – while fully harnessing the reliability and economic value of end-use devices – will require utilities to invest in advanced networking and communications technologies.
Risks When Connecting Over the Public Internet
The U.S. energy sector is already one of the most targeted industries in the world, and cyber-attacks show no signs of slowing down. For example, in 2014, more than 30 percent of malware attacks reported to the Department of Homeland Security were reported by energy companies.
In the Smart Grid space, these security risks are major concerns, because communications from these devices are no longer confined to a boundary of a utility’s controlled network. These devices will be exposed to many new threats, including foreign nations or terrorist organizations who mean to do us harm, as well as so-called ‘script-kiddies’ and ‘hacktivists’ that are trying to make political statements or want to see if they can play with the grid.
Unfortunately, many Smart Grid devices are not truly protected from these threats. Many send and receive messages using unsecured web services, often using proprietary networks for their communications and trusting in ‘security through obscurity’ rather than true protection. These networks rely on a level of implied security, simply because they are a little-known method of contacting end devices. Utilities engaging in these security practices wrongfully believe that because mainstream attackers don’t use the technology, there is little risk of hacks. The truth is, for an attacker who is targeting the system specifically, getting access to the network method is not often technically difficult.
Once an attacker has access to the network method, the question becomes: are there any additional security barriers in their way, and can their presence and activity be detected? Unfortunately, all too frequently, the answer is no.
A Matter of Trust
Proper implementation of security technologies in the Smart Grid is the most important item to consider during manufacturing end-use devices, but it is often overlooked by businesses who are solely focused on functionality. Historically, some level of digital security has been established for communications with Smart Grid devices through the use of self-signed certificates and Private Key Infrastructure (PKI), but there is more work that needs to be done to make the Smart Grid truly secure.
There’s a huge difference between the run-of-the-mill PKI and a PKI done right – with a Certificate Authority (CA) that’s gone through vetting based on rigorous standards. Published standards developed by industry experts help ensure security controls exist to preserve the integrity of the root certificate and confidentiality of the private key. These standards include, for example, North American Energy Standards Board (NAESB) Wholesale Electric Quadrant-012 (WEQ), WebTrust for CAs, and Certificate Authority/Browser (CA/B) Forum.
Regular auditing by a certified auditor on specific and detailed requirements related to business processes, controls, and cyber/ physical security is one of the only ways to ensure a CA is up to par from an outside perspective. The audit reports and/or seals that are fruits of these audits communicate to those relying on a CA’s services that they are, indeed, taking appropriate measures to maintain a secure root. Moreover, these standards ensure that the CA is not just run out of someone’s basement and that the certificates are not merely self-signed.
There are many examples of how careless security practices can undermine the security of a CA, but two in particular that are worth mentioning in depth. Here’s how self-signed certificates and sloppy PKI miss the mark:
- Self-signed certificates are static and cannot, by their very nature, be revoked. Since they never change, any attacker who has gained access to the system can indefinitely monitor the communications and even inject data into what is supposed to be a secure channel.
- Self-signed certificates only reside with the originating server and thus only provide one-way validation. In a secure system, both sides of the communication path would have certificates, proving their identities to one another and fully encrypting the data shared between each entity. In most Smart Grid systems to date, however, end-use devices have not been issued certificates.
- Worse yet, for many Smart Grid end-devices, PKI is generated on the server end and transmitted to a third party during manufacturing to be installed on a device. With this approach, it is impossible to have complete control of the devices’ credentials. You don’t know who they have gone to, or what the manufacturer has done with them. This violates the whole concept behind PKI, which should be generated by the end-user, and never be seen by anyone else.
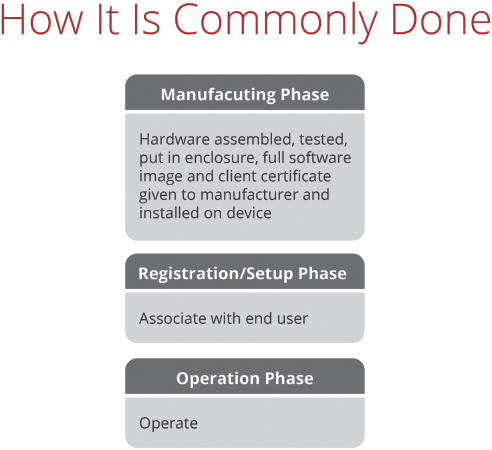
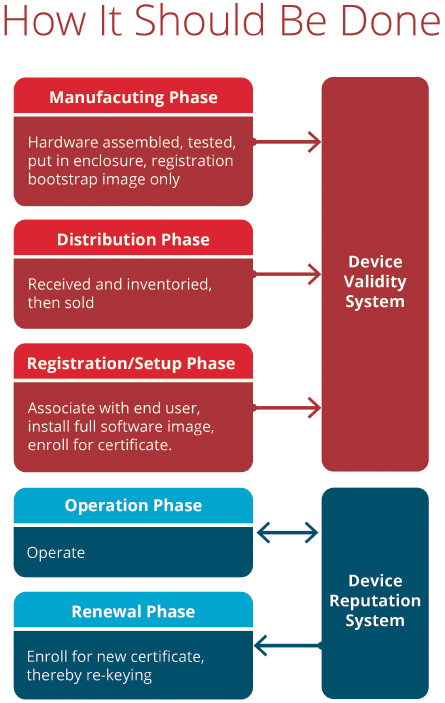
© 2016 OATI, Inc.
Of course, PKI and Digital Certificates are only one part of a comprehensive security strategy that must also include layered physical and cyber security measures with no single point of failure. To fully safeguard their data, and their customers’ privacy, data centers for utility operations must have robust physical security measures, such as fences, video monitors, motion sensors, and biometric scanners, as well as strong cyber security tools, including dedicated fiber channel links, firewalls, and encryption. Additionally, to store and access confidential and proprietary data with complete confidence, utilities must begin to think about building privacy protections into their operations, supply chain management, and more, to ensure security in their vendor management processes.
Better Grid Security with Super Devices
A successful Smart Grid will contain millions of connected end-points and millions of intelligent devices. The only way to securely connect to all of these unknown devices, while maintaining high-level security, is with what we at OATI refer to as a ‘super device.’ A super device is placed at each geographically distinct customer site and can generate its own credentials in the field at the point of installation.
A successful super device should have the following features:
- Communicate with the end-devices via multiple communication protocols, such as Wi-Fi, Zigbee, DNP 3.0, Modbus, or other standards
- Be resistant to physical tampering and have limited device-to-device interactions, where data that do not meet the specified formatting standard are simply discarded
- Be scalable for millions of different devices and technologies
In addition to these functionalities, super devices should be included in a reputation scoring system that monitors data logs from all devices in the field to recognize when a problem is occurring. Devices that do this successfully receive a high reputation score, which tells others they can trust the security of that device.
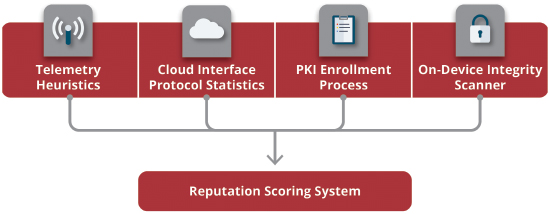
© 2016 OATI, Inc.
Super devices can be connected to a wide area network through the customer site’s existing public Internet, a private network connection, or, for hard to reach locations, by cellular network. Data traffic passing between the super device and the utility control systems is encrypted using PKI protocols, providing a secure and protected communication to and from the field assets.
As the Smart Grid space continues to grow, utilities will need to invest in the high-level security, advanced networking, and communication technologies needed to protect them, and their customers, from the increasing threat of cyber-attacks, in order to fully harness the reliability and economic value of end-use devices. Through the use of super devices, utilities will have an easy-to-deploy, cost-effective solution to confidently and securely connect with end-use devices and leverage their data to improve efficiency and realize additional savings.
About the Authors
 Erik Amundson has more than 17 years of experience in virtually all areas of Information Technology. As Chief Technology Officer of Advanced Systems Design at OATI, Amundson works closely with product development teams and consults on system design and infrastructure. He has extensive experience in technologies and support of advanced data centers such as the OATI Active/Active Private Cloud, OATI GridControl, and OATI GridSafe, which connect the industry’s most stringent cyber security measures, distributed processing, and plug-and-play operations to provide simple, secure, and cost-effective connectivity to grid assets and end-use devices. Amundson received EMC Clarion Training from the EMC Training Facility and is a Cisco Certified Networking Professional (CCNP) and Networking Associate (CCNA).
Erik Amundson has more than 17 years of experience in virtually all areas of Information Technology. As Chief Technology Officer of Advanced Systems Design at OATI, Amundson works closely with product development teams and consults on system design and infrastructure. He has extensive experience in technologies and support of advanced data centers such as the OATI Active/Active Private Cloud, OATI GridControl, and OATI GridSafe, which connect the industry’s most stringent cyber security measures, distributed processing, and plug-and-play operations to provide simple, secure, and cost-effective connectivity to grid assets and end-use devices. Amundson received EMC Clarion Training from the EMC Training Facility and is a Cisco Certified Networking Professional (CCNP) and Networking Associate (CCNA).
 David Heim, J.D., has more than 15 years of experience in the energy industry. As OATI’s Chief Strategy Officer, Heim is responsible for overseeing the Strategic Initiatives department, which includes development of new and emerging hardware and software technologies, development and construction of the new OATI South Campus and Data Center, oversight of OATI’s existing Data Centers and infrastructure, and coordinating compliance with IT-related industry and regulatory standards. Heim began his career as an IT professional for a major international consulting firm. After obtaining his law degree, he joined OATI in the Office of General Counsel, and served as their Chief Information Officer. He received a B.A. degree in International Relations and Chinese from the University of Minnesota and, later, a J.D., Magna Cum Laude, from William Mitchell College of Law.
David Heim, J.D., has more than 15 years of experience in the energy industry. As OATI’s Chief Strategy Officer, Heim is responsible for overseeing the Strategic Initiatives department, which includes development of new and emerging hardware and software technologies, development and construction of the new OATI South Campus and Data Center, oversight of OATI’s existing Data Centers and infrastructure, and coordinating compliance with IT-related industry and regulatory standards. Heim began his career as an IT professional for a major international consulting firm. After obtaining his law degree, he joined OATI in the Office of General Counsel, and served as their Chief Information Officer. He received a B.A. degree in International Relations and Chinese from the University of Minnesota and, later, a J.D., Magna Cum Laude, from William Mitchell College of Law.








